![]()
What is cryptography?
Cryptography is the science of rendering information unreadable to others.
According to a study from Information Week and Price Waterhouse Coopers only few companies use encryption although they know about immediate danger. Is your business relevant information encrypted? This question was answered as follows:
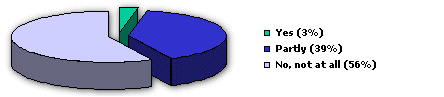
Source: Information Week and Pricewaterhouse Coopers
Encryption systems have been used to protect secrets since millenniums. But they have never been as reliable as today. Modern computer technology, military research, and electronic commerce helped making encryption algorithms freely accessible and documented.
The book Applied Cryptography by Bruce Schneier is one of the most important publications on this subject.
Modern cryptography distinguishes encryption methods in different categories. This does not judge the level of security. The most important category is the distinction between symmetric (secret key) and asymmetric (public key) systems.
If a secret key system (like Steganos) is used a key must be negotiated between communication partners. Programs that base on asymmetric encryption work differently. Imagine a mailbox: everyone can put something in (encrypt) but only the owner can read it (decrypt).
InKA allows you to agree on a key with a communication partner comfortable and securely.
These are the most important encryption algorithms:
| Algorithm | Invented by | Type |
| Blowfish | Schneier | symmetrical |
| DES | IBM | symmetrical |
| Diffie-Hellman | Diffie, Hellman | key agreement |
| IDEA | Lai, Messey | symmetrical |
RC4 |
RSA |
symmetrical |
| RSA | RSA | asymmetrical |
| Skipjack | NSA | symmetrical |
Until now only one system is assumed to be absolutely secure: the one time pad or Vernam-encryption (named after its inventor). As early as 1917 Gilbert S. Vernam who worked for AT&T at this time has invented this system to protect teleprinter communication. Unfortunately this method is rarely applicable because the key used for encryption must be at least as long as the communicated data. Rumors say that the Red phone between Washington and Moscow is secured by a one time pad.
Related topics
Historical
aspects
Recommended reading
InKA: Key agreement
Algorithms used in Steganos
Snake oil
Cryptanalysis
What is Steganography?