
NPS Software
WWWBandit Online Manual
 |
NPS Software WWWBandit Online Manual |
WWWBandit is the definite choice for putting the security of your web sites to the test.
Visit the WWWBandit web site and order now !
Important notice
You should read the License
Agreement.
This program may only be used for testing the security of your own web sites.
This program may NOT be used to gain illegal access to secure systems or web sites.
WWWBandit's outstanding features
|
|
System requirements
Windows 95/98/NT or higher.
Toolbar
File menu
Adding sites to a session
When you enter the URL of a secure site into your browser, most of the time you are
prompted for your username and password in a message box similar to the one below. The URL
that pops up this message box, is the one you should provide WWWBandit with.

When you add a site, WWWBandit will check whether the site is indeed secure. If necessary, WWWBandit will attempt to correct the given URL.
You can attack up to 4 secure sites in a single session.
All attack options can be set independently for each site you add to the attack list.
General attack options
For the Attack Method, you can choose from the standard request methods : HEAD, GET and POST. In most cases, the HEAD method will be your best choice.
You can add a description of the site in the Comment textbox. This comment will be shown during the attack and also in the Found Users dialog.
When you uncheck Stop After One Hit, WWWBandit will continue his search for users until there are no more requests.
The minimum and maximum lengths for the usernames and passwords range between 1 and 24 characters.
![]() Intelligent Session
Intelligent Session
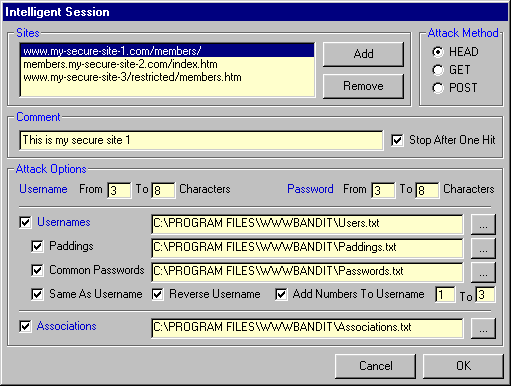
This is the preferred way for attacking a secure site and offers the most chances of success.
Usernames
Here you can specify a list of usernames to be used for the attack. This list will also be
used to derive the intelligent passwords as described hereafter.
Click on ![]() to browse to
the desired paddings file.
to browse to
the desired paddings file.
Paddings
When the username is shorter than the minimal password length, the username will be padded
up to the minimal password length with the strings provided in the paddings file.
Suppose the minimum password length is 6 characters, the username is john and the padding strings are '123456', 'xxxxx' and 'qwerty' then the resulting passwords would be 'john12', johnxx' and 'johnqw'.
Click on ![]() to browse to
the desired paddings file.
to browse to
the desired paddings file.
Common Passwords
Here you can specify a file of passwords that would be appropriate for the type of site.
Click on ![]() to browse to
the desired paddings file.
to browse to
the desired paddings file.
Same As Username
When you check this option, the username will also be used as one of the passwords.
Reverse Username
When you check this option, the reversed username will also be used as one of the
passwords.
e.g. 'nhoj' for 'john', 'dranoel' for 'leonard', 'ruhtra' for 'arthur', etc.
Add Numbers To Username
When you check this option, WWWBandit will create passwords by adding the range of numbers
specified in the two textboxes to the username.
Suppose the username is 'john' and the range is 1 to 3, the resulting passwords would be 'john1', 'john2' and 'john3'.
Associations
Here you can specify a file with combinations of usernames and passwords to be used in the
attack. Each line of this file should contain a single combination in the form
'username:password'.
e.g. 'adam:eve', 'laurel:hardy', 'ginger:fred', etc.
Click on ![]() to browse to
the desired paddings file.
to browse to
the desired paddings file.
![]() Random Session
Random Session
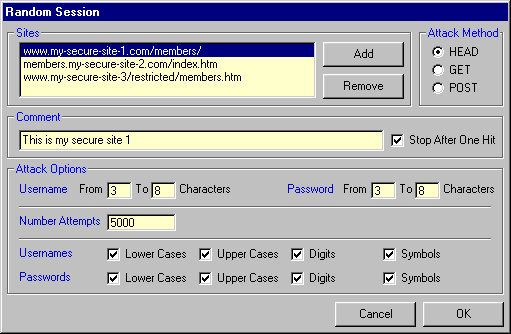
Although it is highly unlikely that you'll ever gain access to a secure site by trying random combinations, this type of attack can give you a deeper insight into the different possibilities of a brute-force attack.
In Number Attempts you can specify how many requests (1 to 999,999,999) WWWBandit should send.
Usernames and passwords may be composed of any combinations of upper and lower case letters, digits and symbols (, . : ; ? ! # $ % & + - * = < > { } [ ] ~ | ^ _). Just check the appropriate options for the usernames and passwords.
![]() Open Session
Open Session
When opening a session, you can either continue the attack immediately or edit the session in the new session dialog. To specify the desired action, select the appropriate radio button.
![]() Save Session
Save Session
Sessions are saved at the current attack position. When an attack is
complete, the session is saved at the beginning in order to retry it on another occasion.
Attack menu

![]() Start
Start
Start the attack after creating a new intelligent or random session or opening a session.
![]() Pause/Resume
Pause/Resume ![]()
Pause or resume the current attack.
![]() Stop
Stop
Stop the current attack.
![]() Current Attack Log
Current Attack Log
After setting up a session, you can review the attack options at any
time.
Options menu
Proxies
You can specify up to 30 different proxies through which WWWBandit can send the requests. The use of anonymous proxies can fool the server under attack into believing the requests are coming from all over the world. You can automatically update your proxies by clicking Update in the proxies dialog.
Agents
Agents are randomly chosen for each new request. This mechanism makes it possible to pretend the requests are coming from different applications (e.g. Netscape, IE, Mozilla, etc.). You can add as many agents as you want.
General Options
By checking Update Proxies On Startup, WWWBandit updates the proxies each time the program starts up.
By checking Log Session, a detailed html log is created for the current session. The log is formatted as follows: URL of the secure site, username:password combination, proxy and returned status code. The colors used for the status codes are: green for OK (200), red for Unauthorized (401) and yellow for all other status codes (e.g. Bad Request (400), Forbidden (403), Not Found (404), etc.). The log is overwritten for each new session.
By checking Stealth Mode, WWWBandit conceals the
attack by sending the requests sequentially. Before starting a stealth mode session, the
program will benchmark the available proxies and pick the best one for the attack. This
mode should only be used when a massive attack results in reporting fake users.
By checking Start Browser On Success, WWWBandit starts your default
browser when a new user is found.
By checking Play Sound On Success, a sound is played to announce a new
found user.
By checking Retry After Complete Timeout, the program will start
resending requests after all proxies have timed out.
By adjusting the slider Refresh Rate Individual Site Info, you can
determine the display rate in seconds for the different sites.
Tools menu
![]() Found
Users
Found
Users
When a user is found, he is automatically added to the list of found users. In the upper listbox, you see the URLs of the cracked sites. When selecting a site, its users appear in the lower listbox. In order to visit a site, click Visit Site or double-click the site or one of its users. To remove a user, click Remove. To remove a site, remove all its users. At any time you can change the comment pertaining to the site.
Merge/Sort Files
This handy feature allows you to manage your user and password
files. You can merge files, remove duplicates and sort them alphabetically.
Help menu
License Agreement
You must read the license agreement and accept all its terms in order to be able to use WWWBandit.
![]() Order Now !
Order Now !
This demo version of WWWBandit will expire after 3 successful attempts. After the demo has expired, you can still use some of its features but you won't be able to start new attacks. Once registered, you will be able to enjoy WWWBandit again to its full extent. On ordering, be sure to supply the exact (you can use copy and paste) 12-character Program Code you can find in the registration dialog (see below). After registering, you will be given a Registration Code to unlock the program.
Register

To register, just paste the supplied Registration Code into the appropriate textbox and click Register.
Copyright ⌐ 1999, NPS Software