![]()
Espionage
A potential attacker can be the colleague in your company as well as service personnel which is ordered to fix a problem in your PC. But who are these professional investigators and what are their aims?
Information that leads to an competitive advantages attracts snoopers most:
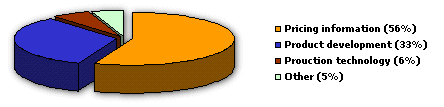
Typical targets of espionage (Source: Heffernan)
Data espionage in the digital age requires well trained and informed personnel. Hackers and secret services meet these requirements.
The hacker
The most well-known group of data thieves are the hackers. They and their sub culture is subject of films like War Games.
Hackers are motivated differently. They are made up by
Articles in the press and other publications often create the impression that hackers are always criminal and 'hacking' is a form of modern organized crime. For most hackers this is not true - they hack because of technical interest and the feeling of adventure.
Secret services
 Secret services are very well organized. Eavesdropping is
their profession. Leader in the field is the National Security Agency (NSA) which employs
more than 37,000 persons. The NSA cooperates with friendly secret services in operating a
world wide surveillance network. This billion dollar project is named Echelon.
Secret services are very well organized. Eavesdropping is
their profession. Leader in the field is the National Security Agency (NSA) which employs
more than 37,000 persons. The NSA cooperates with friendly secret services in operating a
world wide surveillance network. This billion dollar project is named Echelon.
One of the most important surveillance posts is situated in the German town of Bad Aibling. From there NSA eavesdrops wireless communication in central Europe. The biggest surveillance site can be found at Menwith Hill on the British isle - satellites are overheard as well as micro-wave links. Even deep sea wires are not safe from being eavesdropped at - special sub marines are deployed to tap these communication lines.
Echelon automatically searches emails and fax for keywords. Even phone calls are analyzed by digital means. By language detection it is possible to identify the speaking person. In the movie Enemy to the State this technology could be seen - but it actually exists. No matter which device you use Echelon tape-records your call. All gathered information is then analysed by secret service personnel.
There are indications that this collected information is used to reveal business secrets. NSA is suspected to provide US companies with information from competitors.
The source for most of the information about Echelon is the document Development Of Surveillance Technology And Risk Of Abuse Of Economic Information. It has been released by the European Parliament in April 1999.
The book The Codebreakers describes the history of the NSA and other US secret services in detail.
Many companies woo personnel away from government institutions. Creating a private secret service is more or less only a matter of budget and this makes companies able to spy on their competitors.
Related topics