MASKER 5.0
Documentation
MASKER Copyright ⌐ 2000-2001 by Evgueni
Zaretski (SoftPuls.com).
All rights reserved. |
General:
About | Toolbar Buttons
| Security |
User's manual | Help Themes:
Hide Files | Unhide Files | Edit/View
| Change Password | Configuration
|
Info:
Licence agreement | Contact Information |
|
About:
Hide files and have them automatically encrypted!
MASKER is able to hide your sensitive files within
other file (carrier file), which is absolute discrete and looks like regular file without changing the exterior impression.
MASKER encrypts files using strong encryption algorithms (CAST-128, BLOWFISH-256, RIJNDAEL-256, TWOFISH-256).
As a carrier file you can use:
image files (bmp, gif, jpg, tif); audio files (wav, mid, snd, mp3);
program files (exe, dll, ocx); video files (avi, mov, mpg, asf);
For example, you could create a picture file that looks and behaves exactly like any
other picture file but contains hidden encrypted files.
It is not possible to recognize that the carrier file contains hidden files.
Also the carrier file will remain fully functional. Images can be viewed, sounds can be
played and videos can be displayed on the monitor.
Only you, using your password, are able to access the hidden files.
|
Toolbar Buttons:
 |
Hide files: Click on this
button to hide files in a new carrier file. |
 |
Open carrier file:
Click on this button to open a carrier file and to show your
hidden files. |
 |
Extract files: Click
on this button to extract (unhide) hidden files from a carrier
file. |
 |
Add files: Click on
this button to add files to your carrier file. Use this feature to
hide some more files in the same carrier file. |
 |
Delete files: Click on
this button to remove hidden files from a carrier file. The files
which you removes cann't be restored any more. |
 |
File Property: Click
on this button if you want change file names or description of
hidden files. |
 |
Edit/View: Click on
this button if you want to view your hidden files. Hidden files
will be extracted to a temorary folder and opened. |
 |
Change Password: Click
on this button if you want to change the password to access your
carrier file. |
 |
Find carrier file:
Click on this button if you want to search for your carrier files. |
 |
Configuration: Click
on this button to set or change configuration settings. |
 |
Info: Click on this
button to show info window. |
|
Security:
MASKER encrypts files using
strong encryption
algorithms >> CAST 128-bit, BLOWFISH 256-bit, RIJNDAEL 256-bit, TWOFISH
256-bit. That means that your
hidden files are additionally encrypted.
CAST 128-bit: encryption
algorithm designed by Carlisle Adams. It
belongs to the class of encryption algorithms known as Feistel ciphers;
overall operation is thus similar to the Data Encryption Standard (DES).
CAST-128 has good resistance to attack and possesses a number of other
desirable cryptographic properties. It is a good candidate for
general-purpose use wherever a cryptographically strong.
BLOWFISH 256-bit: Blowfish is a
block cipher that was designed in 1993 by Bruce Schneier as a fast, free
alternative to existing encryption algorithms. Since then Blowfish has
been extensively analyzed and no significant weaknesses have been found.
It is considered to be a strong algorithm and has been implemented in
over 130 commercial applications. Bruce Schneier was also one of the
designers of the Twofish algorithm, which is one of the five finalists
selected by NIST in the Advanced Encryption Standard (AES) competition.
Twofish was developed as a successor to the Blowfish cipher, which does
not meet the design requirements of the AES.
RIJNDAEL 256-bit: The block
cipher Rijndael was designed by Joan Daemen and Vincent Rijmen as a
candidate for the Advanced Encryption Standard. It is one of the five
finalists chosen by NIST from a field of 15 candidates as explained
above. The name of the algorithm is a combination of the names of its
two creators. Like all AES candidates, Rijndael is very secure and has
no known weaknesses.
TWOFISH 256-bit: The Twofish
block cipher is Counterpane Labs' candidate for the new Advanced
Encryption Standard. It is one of the five finalists chosen by NIST from
a field of 15 candidates as explained above. Twofish is designed to be
highly secure and highly flexible. It is well suited for large
microprocessors, 8-bit smart card microprocessors, and dedicated
hardware. Counterpane Labs has spent over one thousand hours
cryptanalyzing Twofish, and has found no attacks that can break the
algorithm.
|
Hide Files:
 To
hide files you have to create a new carrier. To
hide files you have to create a new carrier.
Click on this button. This activates the MASKER [Hide] dialog box. |
|
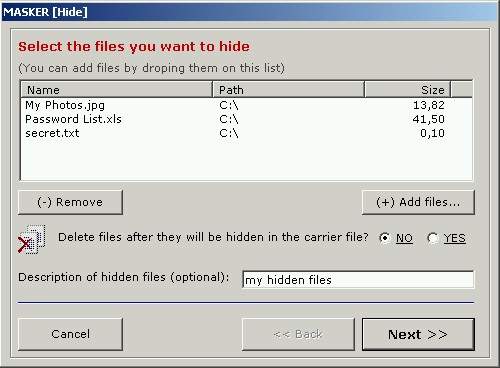
Click on the
"(+) Add files..." button and select files you want to
hide.With the
"(-) Remove" button you can unselect some files. Click the "Next
>>" button to continue.
|
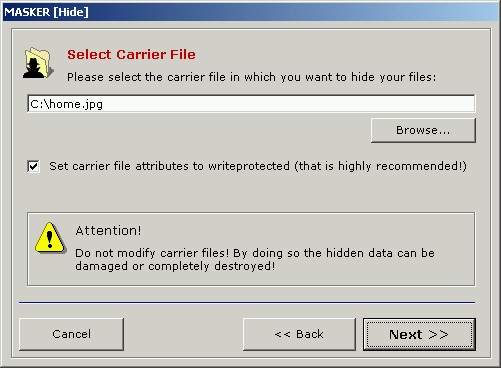
Click on the
"Browse..." button and select the carrier
file. Carrier file is a file in which you hide your files. MASKER 5.0 provides
various carriers: picture files, audio files, program files, video
files.
Click the "Next >>" button to continue.
|

Specify the password
for encryption or carrier file access.
Warning: If you forget the password you will never be able to unhide/decrypt a file.
Then select the
algorithm. If you want to use
compression features then check the "Use compression" box. This will reduce the
carrier file size, but hiding routines will be a bit slower.
Click on the
"Hide!" button to start to hide files.
|
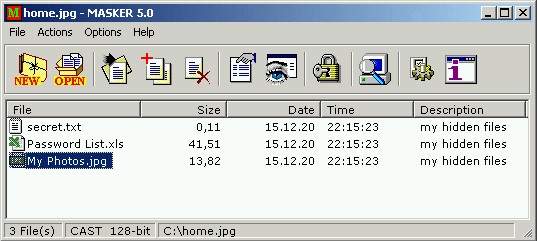
Congratulations! Your files are hidden! |
|
Unhide files:
Congratulations! Your files are unhidden!
|
Edit/View:
 Click
on this button if you want to view your hidden files. Hidden files will be
extracted to a temorary folder and opened. Click
on this button if you want to view your hidden files. Hidden files will be
extracted to a temorary folder and opened.
The View/Edit feature performs these
functions:
1. extracts the selected file to a temporary folder
2. runs the program for viewing this file (e.g. *.txt -> Notepad)
3. saves changes of this file to a carrier file (optional)
4. deletes the file from the temporary folder
|
Change Password:
 Click
on this button to change the carrier file password. Therefor enter the old
password, the new password and confirm the new password. Click
on this button to change the carrier file password. Therefor enter the old
password, the new password and confirm the new password.
Warning: If you forget the password you will never be able to
unhide/decrypt a file.
|
Configuration:
 Click on this button to set or change
configuration settings.
Click on this button to set or change
configuration settings.
|
Licence agreement
MASKER Copyright ⌐ 2000-2001 by Evgueni Zaretski.
All rights reserved.
Evaluation and Registration
--------------------------
This is not free software. You are hereby licensed to use this software for evaluation purposes
without charge for a period of 10 days. If you use this software after the 10 day evaluation period a registration fee is
required.
One registered copy of MASKER may either be used by a single person who uses the software personally on one or more
computers, or
installed on a single workstation used no simultaneously by multiple people, but
not both.
Warranty
---------
This software and the accompanying files are sold "AS IS" and without warranties as to performance or
merchantability or any other warranties whether expressed or implied.
Because of the various hardware and software environments into which MASKER may be
put, no warranty of fitness for a particular purpose is offered.
This application has been created for the protection of your sensitive documents and
programs, it is not meant for illegal activity. This
software is not responsible for any criminal, legal, civil or other type of
harm that may come to you for misuse of this software. This software implies no
warranty, guarantee, or responsibility for damages of any
kind to you or your computer. You agree to hold this software and staff
harmless in an event of software failure, damage or loss of files, or damage to your computer system.
Distribution of Evaluation Version
-------------------------------
Provided that you verify that you are distributing the evaluation version you are hereby licensed to make as many copies of the evaluation
version of this software and documentation as you wish; give exact copies of the original evaluation version to
anyone; and distribute the
evaluation version of the software and documentation in its unmodified form via electronic
means. There is no charge for any of the above.
You are specifically prohibited from charging, or requesting donations, for any such
copies, however made; and from distributing the software
and/or documentation with other products (commercial or otherwise)
without prior written permission.
|
Contact Information:
Developer: Evgueni Zaretski
(SoftPuls.com)
Internet: http://www.softpuls.com/masker
|





