
summary of a typical scan result.
|
Scan-results
| [Previous] [Main] [Next] |

summary of a typical scan result.
| · | Summary - This section will give you a running total of the following (from left to right):
| |
|
| ||
| 1. | Running Processes - This is a report of the total number of processes that are running concurrently while Ad-aware is performing a scan. This is nothing to be concerned about unless it is excessively high (this may slow down the scan). This is here for your information and the details of these processes are included in the final log file report.
| |
|
| ||
| 2. | Objects recognized - This is a running TOTAL of all the recognized objects detected.
| |
|
| ||
| 3. | Objects ignored - This is a running total of all objects that will be ignored because the user has added them to their Ignore list. Ignored items will be listed as "Objects ignored". They will not be shown in the scan result-list and will be unavailable for deletion.
| |
|
| ||
| 4. | New Objects - This keeps a running total of all newly (unexpected) detected items, that are not on the Ignore list.Ad-aware will count all detected content as new except for those objects in the Ignore list (which it will see as old).Removing them from the Ignore list will force Ad-aware to see them as "new objects".
| |
|
| ||
| 5. | Detected content breakdown - This is the larger section on the right side. You will see the following:
| |
| · | Processes identified - This is the total number of detected processes. This is different from the total number of running processes in that this only lists the number of those that are targeted and/or dangerous.
| |
| · | Registry keys identified - This is the total number of targeted or suspicious registry keys.
| |
| · | Registry values identified - This is the total number of suspicious registry values. Please note that this is different from the number of keys because content may have been added to existing, legitimate keys.
| |
| · | Files identified - This is the total number of suspicious files.
| |
| · | Folders identified - This is the number of suspicious folders.
| |
| · | 34 Processes currently running on the system, none are recognized as a target.
| |
| · | 33 Objects recognized 'total', including 11 registry keys and 22 files.
| |
| · | 0 Objects from the ignore list detected during the scan.
| |
| · | 33 New (unexpected) objects.
| |
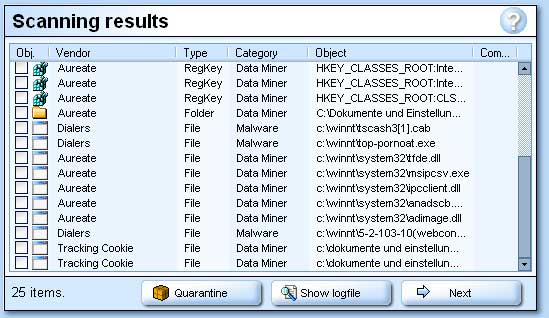
The scan-result list, use the right-mouse button to open the list menu
| · | Item Details - Displays the full details of the selected item.
| |
| · | Select all objects - Selects all objects in the list.
| |
| · | Deselect all objects - Deselect all objects in the list.
| |
| · | Inverse selection - All checked objects become unchecked and all unchecked objects become checked.
| |
| · | Select all 'Vendors name here' objects - Selects all objects in the list matching the vendors name.
| |
| · | Deselect all 'Vendors name here' objects - Deselects all objects in the list matching the vendors name.
| |
| · | Check\Uncheck all "Object type here" objects - Selects all or none of the objects in the list matching the object type.
| |
| · | Extensions - Allows access to currently installed Plug-ins.
| |
| · | Quarantine selection - Creates a backup of the selected item.
| |
| · | Add selection to ignore list - Adds the selected items to the 'Ignore list'.
| |
| · | Jump to key - Activates RegHance (if installed and the file path set) and takes you to the selected area within your registry.
| |
| Note:This feature requires that RegHance be installed, and does not work with the native Windows registry editor.
| ||
| · | Export registry bookmark file - Generates a Registry Bookmark file of the currently selected registry entries.
| |
| · | Show properties in Explorer - (Files and folders only) Opens the Explorer propertie's dialog for the selected object.*
| |
| · | Open folder in Explorer - (Files and folders only) Opens the folder containing the object in Explorer.*
| |
| · | Export HTML report - Allows you to save a report of the current list in HTML format.
| |
| · | Export as text document - Allows you to export a report of the current list as a plain text file.*
| |
| · | Print Report - Allows you to print a report of the current list. *
| |
| · | Help - Opens the Ad-aware 6 user manual.
| |
| · | Quarantine - Creates a backup of the selected items.
| |
| · | Show logfile - Displays the current Ad-aware log file.
| |
| · | Finish - Deletes the selected items and completes the scan/removal process.This will also quarantine the selected items if the option "Automatically quarantine objects prior to removal" is set.
| |
|
| |
| · | Right click in the results windows for additional options.
| |
|
| |
| · | Right click on a detected item and select "extension" to perform additional tasks and execute installed extensions.
| |
|
| |
| · | To keep an item on your system and remove it from being flagged in future scans, place it in the "Ignore list" using the related menu entry.
| |
|
| |
| · | Note : Items moved to the ignore list will be removed from the result-list.They are still active and running on your system.
| |
| · | It's recommended to create quarantine archives (isolate and backup) prior to removing any items!
| |
|
| |